Table of Contents
Human component in cyber security is a very crucial aspect of security and the majority of cyber-attacks are targeted towards humans. There are cyber security attack trends focusing on certain groups of individuals such as leadership, or targeted attacks on specific individuals in organizations. As per Gartner prediction by year 2025 more than 50% of cyber incidents would be the result of lack of right talent or human failures. Majority of such targeted attacks use phishing as a handler to gain access to company’s data and systems. Email is the most common medium in such attacks but other mediums are also widely used nowadays such as Phone, SMS etc.
Today we look more in detail about Cyber incidents related to phishing and token compromise, how such attacks are scaled, planned, and executed and what could be possible ways which could help to remain protected from such attempts.
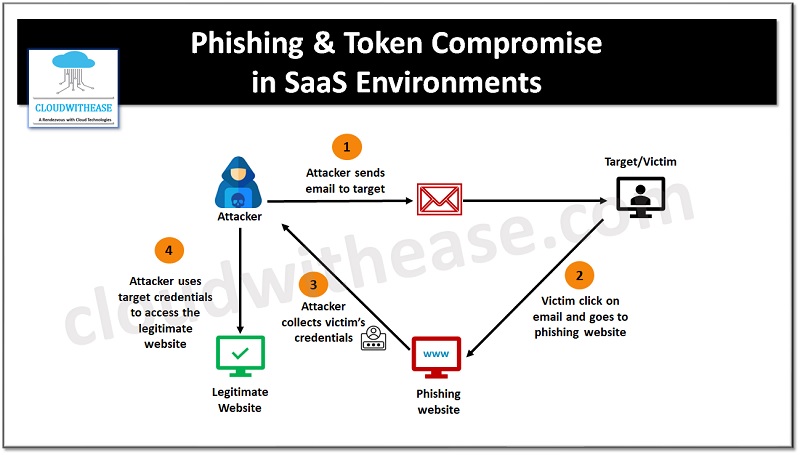
Understanding a Phishing Attack
The phishing attacks often use social engineering techniques to gain trust of targets before duping them. Emails, text messages, or instant messages are common forms of phishing attacks.
The incident started with a phishing email which was offering enrolment in company benefits. The email which was sent looked legitimate with an external domain, including recipient full name, clear date, and time for enrolment. While generating a sense of urgency. The user considering it legitimate logged in using SMS and Multi factor authentication.
After realizing the mistake, a few minutes later the user was unable to reset their password and existing session and the attacker had gained the access while Microsoft Defender O365 was unable to detect the attack.
When investigation initiated into target accounts from different AWS data center, it was found that several parallel sessions existing between target and hacker during the said period.
On connecting client environment two significant threats were emerged related to:
- Reuse of session token – Target SaaS session was re-used with a technique which is otherwise difficult to identify having a proper tool in hand.
- Malicious MFA enrolment – Hackers usually try to add / enroll their MFA devices for control. This technique was used here where a bad actor had registered a new mobile as MFA factor.
The email submission for rescan when came to the system administrator, it came back marked as safe.
How to Remain Secure?
There are several techniques used against SaaS environments and MFA to gain access to target systems. There are security recommendations which could prevent such attacks as described below.
- Social engineering techniques- such as the common technique of phishing with humans. The robust security awareness programs often fail in phishing attacks. Implementation of stronger MFA mechanisms WebAuthN could be a stronger reason for usage. Use of phishing resistant MFA based on public key cryptography , elimination of shared codes, and disabling hacker ability to intercept credentials, limiting authentication action could be some possible techniques to hamper phishing attempts.
- Bulletproof initial lines of defense – The failing of initial scans of emails for identification of phishing needs to be looked at more in depth to understand where it failed and why the system was not able to detect phishing attack and MFA breach.
- Threat detection is a critical capability to be considered – Several security measures which are persistent in nature make the SaaS environment discreet and secure. Threat detection mechanism shall help security teams to address such situations and limit the breach.
Practices to consider if hit by a Phishing Attack
We look at some practices if there is an indication of phishing compromise or fallen to hacker:
- All user attributes such as phone numbers not changed in phishing attack
- Suspicious transactions activity logs for account
- Check with employees if they have found something suspicious or tried to click some link etc.
- Do perform a forensic analysis to look into relevant system logs for any indications of compromise , firewalls log for suspicious activities, unrecognized URLS or IP addresses, headers and attachments in phishing mail , logs of audit tool for any suspicious activity recorded or any security events generated related to privilege accounts access
- SPAM filters and scan settings to ensure messages are getting blocked having malicious contents
- Inform and educate all employees for future attacks and raise the bar of general awareness around identification of phishing attacks
