Digital transformation is driving hybrid cloud adoptions within enterprises. Many businesses are adopting multi-cloud strategy to utilize capacity and functionalities in offering from several cloud providers. This helps organizations to choose services which fits well to their needs. However, multi-cloud strategy requires robust multi-cloud security strategies as well to effectively secure and protect data and resources across hybrid cloud environments
Today we look more in detail about multi-cloud environments, multi-cloud security threats, multi-cloud security best practices and challenges.
Introduction to Multi-Cloud Security
Multi-cloud security is a critical aspect of cloud computing and its associated workloads and services. As businesses are increasingly adopting multi-cloud architectures to leverage benefits of several cloud providers, save costs and reduce dependencies for services on single cloud providers, the complexity of multi-cloud environments security is a major concern.
Multi-cloud security refers to policies, procedures, and technologies implemented for protection of data, applications, and resources across multiple cloud service providers. It ensures confidentiality, integrity, and availability of resources in hybrid cloud environments at the same time ensuring compliance with relevant regulatory requirements.
Each cloud provider has a unique set of security controls, compliance requirements, and threat profile. The comprehensive approach involves identification of risks associated with each cloud provider platform, implementation of security controls to address those risks and monitoring the environment for any potential security issues.
Related:
6 Multi-cloud Architecture Designs for an Effective Cloud Strategy
Multi-Cloud Security Threats
When we design a security plan for multi-cloud environments, we need to identify several threat sources. Let’s look at some of the common threats in multi-cloud environments.
- Management of security policies, access control, and monitoring across multi-cloud environments is a challenging tasks in the absence of unified governance
- Security policies and procedures inconsistencies across cloud environments arise due to silos, staff constraints, lack of sufficiently skilled staff etc.
- Protection of workloads across becomes critical irrespective of where they are hosted and which calls for consistency in security policies and procedures across cloud environments
- Different cloud providers use different APIs and protocols which could lead to interoperability concerns
- Misconfigurations or drift configurations could occur when changes made in one cloud environment but not replicated across
- Lacking visibility across environments – detection of security incidents across all cloud environments could be a challenging task without proper monitoring and tracking tools
- Consistency in access controls becomes critical in multi-cloud environments having strong authentication and authorization policies
- Shadow IT – could occur when business units bypass IT and use cloud services
Multi-Cloud Security Strategy
Multi-cloud strategy requires deep understanding of potential risks and threats across cloud environments. Let’s look at some key elements to be considered while developing security strategy for multi-cloud environments.
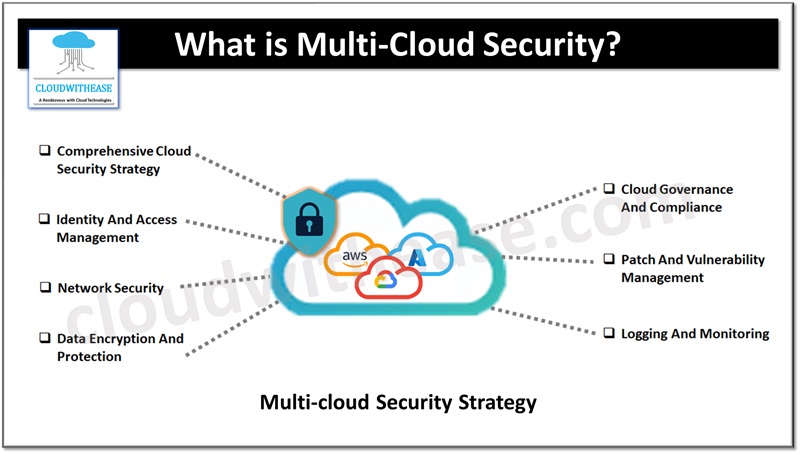
- Critical assets and data identification – start identification of critical assets and data which require protection. Critical assets include sensitive customer data, financial data, intellectual assets etc.
- Assessment of risks and threats – post identification of critical assets assesses risks and threats landscape for those assets , external threats, supply chain threats, and vulnerabilities in your applications and infrastructure
- Decide the security framework to use – choose a security framework which aligns to organization goals and objectives related to compliance.
- Implementation of security controls – implement security controls align to chosen framework such as access controls, network segmentation, encryption, data loss prevention etc
- Monitoring and testing – regular monitoring and testing is major aspect of multi-cloud strategy to ensure effectiveness of implemented controls
- Planning incident response – develop and incident response plan which outline steps to handle a security incident
- Regular testing of security – test security strategy often to identify vulnerabilities and assess the effectiveness of implemented controls
- Up to date with current security trends – stay up to date on latest security threats and trends. This is required to re-align or adjust security strategy as per the changing requirements.
Best Practices Multi-Cloud Security
Some of the best practices are listed here which would help to ensure security of multi-cloud environments.
- Using a unified management and governance platform helps to enforce consistent policies across all cloud service providers and simplify compliance reporting and reduce risk of cloud misconfigurations
- Comprehensive identify and access management strategy – includes role-based access control , multi-factor authentication and centralized management for user accounts
- Encryption for data at Rest and in Motion – encryption is critical component of cloud security ;as it helps in protection of sensitive data from unauthorized access
- Monitoring and analysis of logs and events – monitoring logs and events help in early detection of security incidents and to formulate quick response
- Conducting vulnerability assessments and automated penetration tests – help to identify potential vulnerabilities in infrastructure and applications
