Table of Contents
No matter if a company uses cloud services or not, security is an issue that needs to be addressed. Possible threats include denial of service, malware, SQL injection, data breaches, and data loss, all of which can have a major impact on a business’ reputation and financial success.
Switching to the cloud brings about new potential hazards, as well as transforming existing ones. Nevertheless, this does not imply that cloud computing is unsafe. On the contrary, many cloud suppliers supply access to highly sophisticated security tools and resources which you would be unable to access otherwise.
It is essential to be conscious of the potential risks that come with cloud computing in order to reduce their impact. Therefore, let’s analyze the special safety issues related to cloud computing.
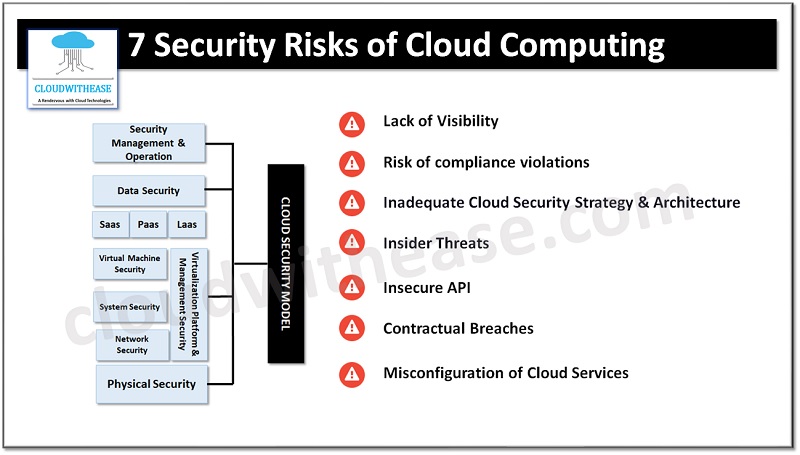
Possible Security Risks of Cloud Computing
Lack of Visibility
A lot of companies take advantage of different cloud services on a variety of devices, in different departments and in different parts of the world. Without the necessary tools, this level of complexity in a cloud setup can lead to a lack of visibility in terms of access to the infrastructure.
Without the right protocols in place, it can be difficult to keep track of who is utilizing your cloud services and what data they are downloading, accessing, and uploading. If there is no visibility, then it cannot be ensured that the data is safe and secure, making it more likely that a data breach or data loss will occur.
Risk of compliance violations
With more and more rules and regulations in place, it is necessary to comply with a variety of rigid demands. If you switch over to the cloud without being watchful, you might breach the compliance regulations.
A lot of these regulations necessitate that your business is aware of where its data is located, who has access to it, how it is handled, and how it is protected. Other regulations demand that your cloud service provider has specified credentials to remain compliant. Any negligence in transferring data to the cloud or making a bad choice of cloud provider can make your business in breach of regulations. This can potentially result in legal and financial repercussions.
Inadequate Cloud Security Strategy and Architecture
Companies often move their systems and data to the cloud without taking the necessary precautions to protect their infrastructure, as they are eager to get started with operations. You can prevent this particular risk associated with cloud security without much effort.
It is essential to establish a security plan and architecture that has been tailored to the cloud before you commence operations with your systems and data. There are many migration service providers available in the market to ensure a smooth and safe move to the cloud, as well as avoid any extended periods of downtime.
Insider Threats
People you trust such as your employees, contractors, and collaborators can potentially be a risk to your safety measures. In the majority of cases, these insider threats are caused by negligence or lack of education rather than ill will. Migrating to a cloud provider will introduce a new risk of internal security breach due to actions of the provider’s personnel.
Insecure API
When running systems in a cloud setup, you can apply an API to maintain control. Any API integrated into your web-based or mobile applications can give either internal staff or external customers’ access. APIs that interact with external sources can present a potential security hazard. Any API with inadequate protection can act as an entry point for cybercriminals, allowing them to take data and tamper with services.
Probably the most well-known instance of an exposed external API is the Facebook – Cambridge Analytica Controversy.
Contractual Breaches
Any agreements you have in place will have particular regulations on the usage, storage and permission for access of any common information. If your staff unknowingly transfer restricted data to a cloud service without permission, it could violate the contract and cause possible legal consequences.
It is essential to carefully examine the terms and conditions of your cloud services provider. Even if you have the approval to transfer data to the cloud, certain suppliers may contain a clause that allows them to share the information that is put into their system.
Misconfiguration of Cloud Services
Incorrect setup of cloud services can be a security risk. This problem is growing, particularly because the range and variety of services have become more extensive. If the cloud services are misconfigured, information could be made publicly available, altered, or eliminated.
What is the best way to manage Cloud Security?
Due to the fact that the cloud security needs of each organization are different, it is important to consider various factors. To help with this, the National Institute of Standards and Technology (NIST) has compiled a set of recommended guidelines that can be implemented to create a robust cloud computing infrastructure.
These guidelines are based on the NIST’s five fundamental elements of cybersecurity: Identify, Protect, Detect, Respond, and Recover. Organizations should take the time to analyze their own security readiness and incorporate suitable preventive and recovery safety measures into their systems.
