Table of Contents
With an ever-increasing number of organizations shifting to the cloud, the need for reliable cloud computing has been growing. AWS Identity and Access Management (IAM) is a service that AWS provides to help keep your cloud-based data protected through its authentication and authorization processes.
In this blog, we will understand the basics of AWS Identity and Access Management service, its working, components, features, use cases etc.
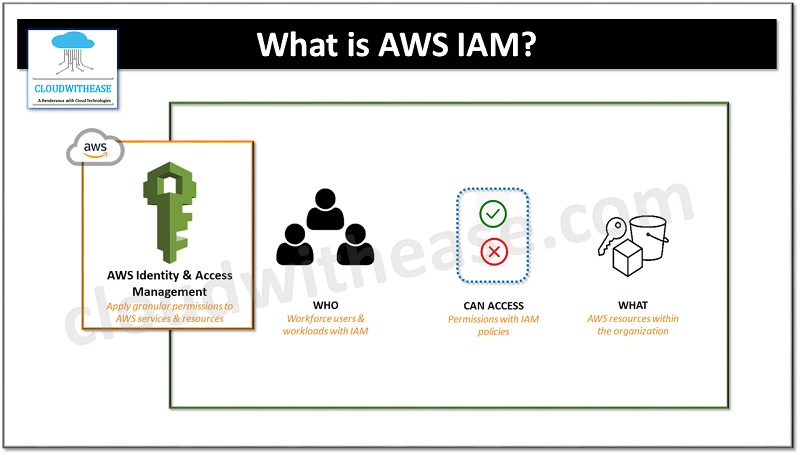
What is AWS IAM?
AWS IAM enables you to administer access to AWS services and resources securely. It allows you to create groups of users who can be authorized to access specific servers, or on the other hand, who can be denied access to the service. It also gives you the ability to control Root Access Keys, set up Multi-Factor Authentication for extra security, and much more.
What is the need to use AWS IAM?
IAM can be employed to manage and scale the access of workload and personnel in a secure manner, enabling you to become more agile and innovative.
Generally, in the corporate realm, granting permissions and access is an extended task. It’s normally the IT administrators who have the passwords, and if you want to make any alterations, you have to make a request to them. Most times, the passwords are all the same. IAM service resolves this problem and adds security levels. Moreover, it also provides a secure way to share resources. The users are authenticated and given permissions in accordance with their need, and you can regulate who has access to your resources and to what degree.
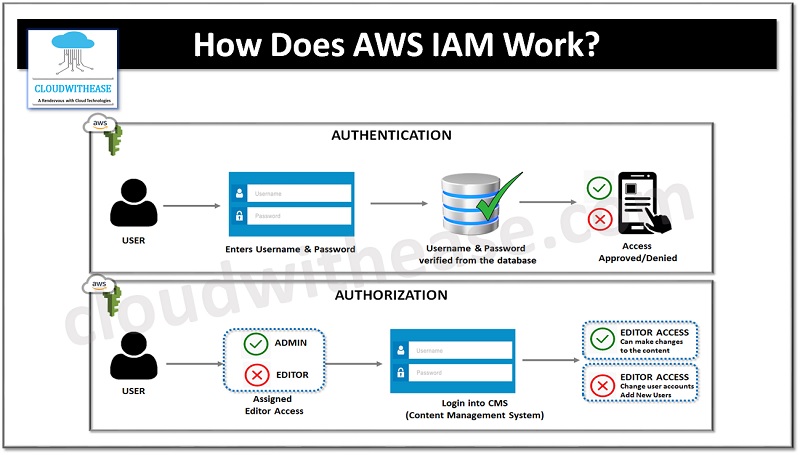
How Does AWS IAM Work?
The workflow of IAM encompasses six components, which are as follows:
- Principal: An entity with the ability to take action on an AWS resource can be referred to as a principal. The principal can be a user, role, or application.
- Authentication: To gain access to an AWS product, it is necessary to confirm the identity of the user. This process is known as authentication and requires the individual to offer proof of identity by providing their credentials or assigned keys.
- Request: A principal must send an inquiry to AWS, with specifics of the resource they are intending to use and the activity that needs to be accomplished.
- Authorization: As a rule, all resources are denied permission by default. IAM will only accept a request if it meets the requirements of an applicable policy. After both authentication and authorization of the request are confirmed, AWS will give the go-ahead for the action to take place.
- Action: A decision must be made in order to determine if it is necessary to view, edit, create, or delete a certain resource.
- Resources: It is possible to perform a set of actions on a resource associated with your AWS account.
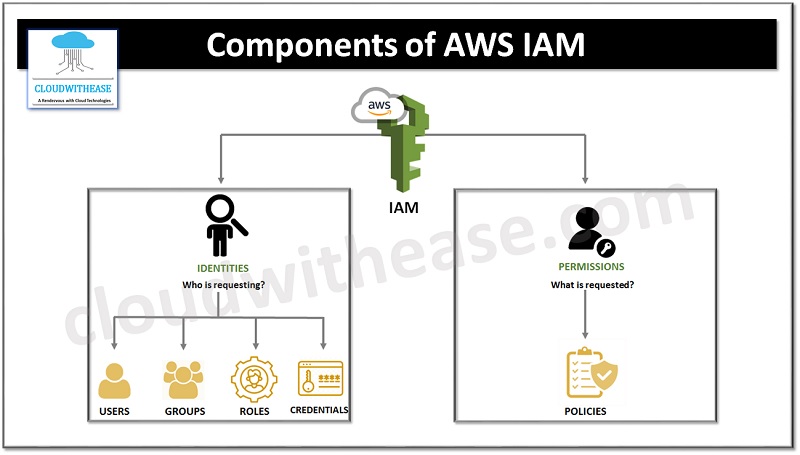
Components of AWS IAM
There are 4 basic components of AWS IAM, namely users, groups, policies and roles. Let’s explore them in detail.
Users
IAM user is an identity possessing a credential and related authorization. It could represent an individual or an application. Through IAM, one can ensure secure access to AWS services by establishing a single IAM user name for every employee in your firm. Each IAM user is exclusively associated with one particular AWS account. By default, a freshly generated user is not allowed to execute any action in AWS. The advantage of having one-to-one user specification is that you can provide specific permissions to every user.
Groups
IAM groups are composed of various IAM users, allowing distinct permissions to be given to the whole group. This way, administrators can easily grant permissions to one group and it will be automatically applied to each individual user in the group. Furthermore, if a new user is added to the group, they will also receive the same permissions and policies without any extra effort. This helps to reduce the workload of administrators.
Policies
IAM policies are stored as JSON documents in AWS and they provide authorization for users to access AWS resources. These policies specify which user can get access to what resources, the actions they are permitted to carry out on the resources, and when they are allowed the access. The two types policies are:
- Managed Policy: A managed policy is a pre-configured default policy of AWS that can be applied to various entities such as users, groups, and roles in an AWS account. These policies, either created by AWS or by customers, are independent identity-based policies that can be attached to multiple users and/or groups.
- Inline Policy: The customer(s) create an inline policy which is included in a single entity.
Roles
IAM roles establish which activities can be denied or permitted by any entity on AWS. This is done in the form of permissions. Such permissions can be accessed by any entity on AWS, and temporary credentials are issued as part of these permissions.
AWS IAM: Key Features
- Shared Access: The fundamental characteristic of IAM is that it empowers you to devise one of a kind usernames and passwords for separate users or resources and assign access to them.
- Identity Federation: Individuals can verify their identity by utilizing other accounts like Facebook or Google. This authentication can be trusted by IAM and access to individuals can be given based on those accounts. Users can also make use of this to keep the same password for their site and the cloud.
- Specific Permissions: Policies can be imposed to limit certain requests. For example, a person can be given read-only access to a certain piece of data but will not be allowed to modify it.
- Multi Factor authentication: MFA (Multi-Factor Authentication) makes it easy to provide an extra layer of security for both your account and individual users. Users can submit their login information and a one-time code sent to their mobile phones for verification.
- PCI DSS compliance: The Payment Card Industry Data Security Standard is a safety protocol for organizations who deal with credit cards from the leading card agencies. AWS IAM is PCI DSS compliant.
- Password Policy: With the IAM password policy, it is possible to reset or modify passwords from a distance. Additionally, regulations can be imposed, for example, the criteria a user must follow when selecting a password, or the maximum number of times a user can attempt to enter a password before it is declined.
- Open source: AWS IAM is an open source service. No extra fee is incurred for utilizing IAM security. There is also no cost associated with adding additional users, groups, or policies.
Final Words
With the increasing popularity of AWS Cloud, there is a growing demand for professionals with expertise in the Amazon Web Services. Of all the security measures the company has put in place, the Identity and Access Management (IAM) has been deemed the most beneficial, as we have already noted in the blog. The need for online security makes IAM a prime factor when it comes to AWS.
