Table of Contents
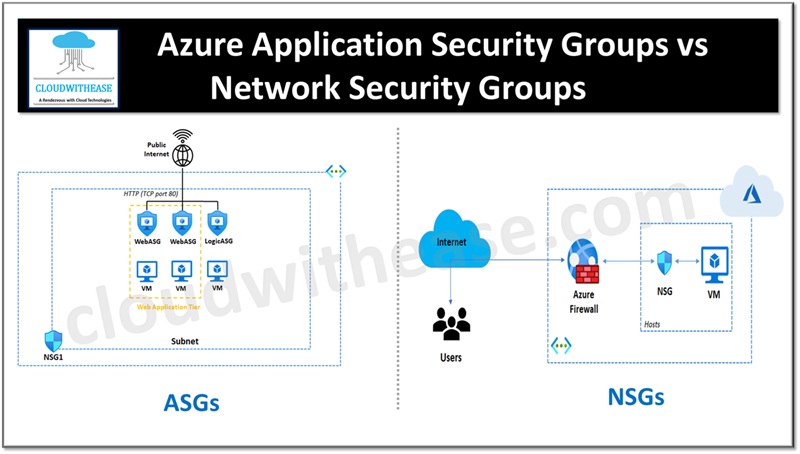
Azure ASG (Azure Application Security Group) allows you to group VMs logically and apply network security rules based on those groups. Whereas, Network Security Group (NSG) contains the actual security rules that control inbound and outbound traffic to resources.
Accelerated pace of digital transformation leads to more and more organizations moving their workloads to the cloud but at the same time there is a rising concern over security of data over cloud. Organizations looking for a security model which effectively adopts the complexity of the modern era and embrace hybrid working model which protects applications, services and data hosted across cloud and on prem environments.
In today’s article we understand and compare Application Security Groups and Network Security Groups provided by a leading cloud provider Azure to ensure data security over cloud, purpose of each, difference between the two terminologies and use cases.
Azure Application Security Groups
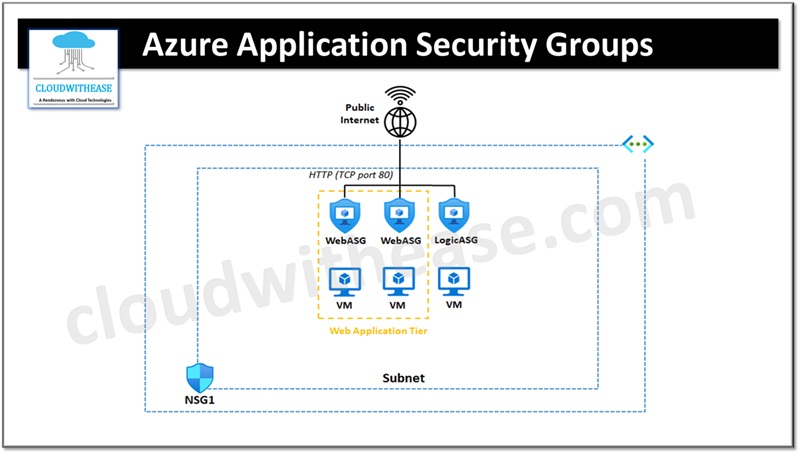
Azure Application security groups (ASGs) are used to enable configuration of network security as a natural extension for application architecture allowing grouping of virtual machines and defining network security policies on the defined groups.
- We can reuse the security policy at a scale without the need for a manual maintenance of explicit IP addresses.
- The explicit IP addresses complexity is taken care by platform and numerous rule sets allow it to be focused on actual business logic.
- ASGs provide the capability to deploy multiple applications within the same subnet and traffic isolation on the basis of ASGs.
Network Security Groups (NSGs)
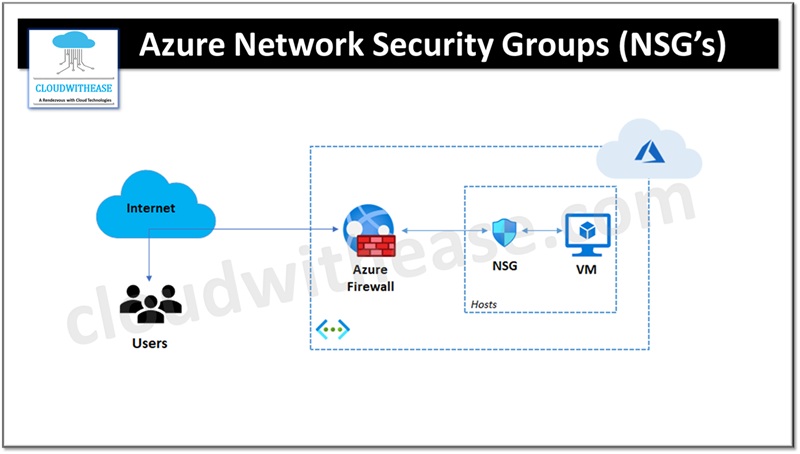
Azure Network security groups (NSGs) are used to filter network traffic in Azure virtual network to and from Azure resources.
- We can set up security rules to allow or deny inbound/outbound network traffic from various Azure resources.
- For every rule defined in NSG we have to specific source, destination, port and protocol.
- Security rules are evaluated and applied on the basis of five tuple namely source, source port, destination, destination port, protocol).
- We can’t create two security rules having the same direction and priority.
- For existing connections flow rules are created. Communication is allowed or denied based on the state of connection in flow record. The flow record makes NSG stateful.
- Inbound traffic processing happens in specific order as such Azure processes rules in the network security group associated to subnet first if available, then to network interface, including Intra-subnet traffic as well.
- Outbound traffic processing happens in specific order as such Azure process’s rules in network security group to network interface first, then to associated subnet, including intra-subnet traffic as well.
Comparison: Azure ASG vs NSG
Below table summarizes the difference between the two terminologies:
| Parameter | Azure Application Security Groups (ASG’s) | Network Security Groups (NSG’s) |
|---|---|---|
| Terminology | Enablement to configure network security as natural extension for application architecture | Network traffic filtering between Azure resources in virtual networks and subnets. |
| OSI layer | Operates at transport layer of OSI model | Operates at network layer and transport layer of OSI model |
| Purpose | Designed to secure application components and enforce security policies specific to application tiers | It is used to apply security rules to control traffic based on IP address, source, destination port and protocols |
| Configuration | Operates at VM level, performs grouping of VMs and define security policies based on the groups | Operates at host level. They are assigned on subnet and network interface level. |
| Features | * Rules are applied at ASG’s in same virtual networks * ASG’s can be specified within all security rules of NSG limit with limit of 100 NSG rules * Inbound/outbound traffic is controlled at subnet level * Basic security controls and segmentation within virtual network is provided | * Rules are applied to all resources in an associated subnet * NSG has 100 rules limit * Inbound/outbound traffic is controlled at network interface level |
| Use cases | * Group virtual machines based on requirement of applications * Application level granular security control * Scalability and ease of rules management for NSG’s * Flexible association between ASG’s and NSG’s * Agility to manage security policies | * Access restrictions to specific ports and protocols * Role based access control implementation * Segmentation of virtual networks and control communication between subnets * Protection of virtual machines from inbound malicious traffic * Enforce security policies |
Download the comparison table: Azure Application Security Groups vs Network Security Groups