Table of Contents
Cloud based networking replaces network hardware appliances with virtual machines. The virtual machines used as hypervisor run networking software and processes such as load balancers and routing. This eliminates the need for buying new networking hardware and provides flexibility and scalability to provide network operations to provide new services on demand.
In today’s topic we will learn about Cisco NFV terminology, its architecture and function, its advantages and limitations.
What is Cisco Network Functions Virtualization
The Network function virtualization uses virtual machines instead of network appliances. This standard was proposed at OpenFlow World congress in the year 2012 by a group of service providers that includes AT&T, China Mobile, BT Group, Deutsche Telekom, and many more and also known as the European Telecommunications Standards Institute (ETSI). NFV helps in separation of communication services and eliminates need for new hardware and provides new services on demand. With NFV it is possible to deploy networking components quickly in a matter of few hours instead of months with networking in traditional setup.
Advantages of Network Function virtualization
- It follows pay as you go model and less expensive
- Less equipment with virtual setup
- Scalability of network architecture is quick and simpler using NFV virtual functions
Related: Server Virtualization vs Network Virtualization
Cisco NFV Architecture
The NFV software handles tasks of networking components related to load balancing, routing, firewall security. The provisioning can be automated on a virtual network using a program and its components with a hypervisor or software-defined-networking controller.
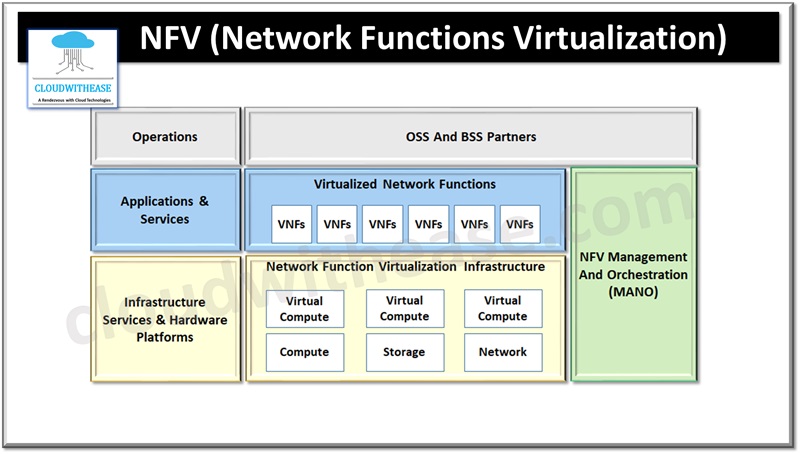
The virtual layer and hardware environment are provided by Cisco Network Function Virtualization Infrastructure (NFVI) for operations. VNFs provide network specific functions such as routing, load balancing, network detection, domain name services (DNS), caching, network address translation (NAT) etc. these network functions required a strong integration between network hardware and software in traditional networks however, with VNF’s they facilitated decoupling (loosely coupled) of underlying hardware and software.
Cisco NFVI has a virtual infrastructure layer (Cisco VIM) which embed the Red Hat OpenStack Platform (OSP 10). Cisco VIM has the Newton release of OpenStack, the open source cloud operating system capable of controlling large pools of – computing, storage and networking resources. The OpenStack compute, network, and storage services, and all NFVI management and control functions are managed by Cisco VIM. Key Cisco NFVI roles and their functions are:
Control (including Networking) – provides Maria Database/Galera, RabbitMQ, HA Proxy/Keepalive, Identity Service, Image Service, Compute management, Network service, Storage service, Horizon dashboard and Fluentd
Compute – provides compute service and virtual Networking Service
Storage – provides storage services.
Management (including logging, and monitoring) – provides Cisco VIM Installer, Cobbler server, Docker Registry and ELK server
Network Function Virtualization: Associated Risks
- Physical security measures such as locking down critical network components do not work here
- Malware isolation and its containment is difficult as it travels more easily among virtual components running on same virtual machine
- It is difficult for network monitoring tools to detect potentially malicious anomalies in the network going east-west between virtual systems it requires more fine-grained controls to do so
How does NFV differ from Traditional Network Architecture?
In traditional network architecture, network functions (such as routers, firewalls, and load balancers) are implemented on dedicated, purpose-built hardware appliances. NFV, on the other hand, virtualizes these functions so they can run on standard, off-the-shelf hardware. This allows for greater flexibility, scalability, and reduced costs compared to traditional, hardware-based networks.
NFV vs VNF: What is the difference?
| Aspect | NFV (Network Functions Virtualization) | VNF (Virtual Network Function) |
| Definition | Overall framework and architecture that virtualizes network functions traditionally run on dedicated hardware. | Actual software instance of a network function that runs within the NFV framework. |
| Scope | Entire ecosystem including infrastructure, management, and orchestration. | Represents individual network functions like routers, firewalls, or load balancers that have been virtualized. |
| Components | Includes Virtual Network Functions (VNFs), NFV Infrastructure (NFVI), and Management and Orchestration (MANO). | VNFs are components within the NFV architecture and require NFVI and MANO for deployment and management. |
| Functionality | Provides the framework and infrastructure for deploying, managing, and orchestrating VNFs. | Performs specific network functions (e.g., routing, firewalling, load balancing) in a virtualized environment. |
| Objective | To virtualize network functions and decouple them from physical hardware, allowing for flexibility, scalability, and cost-efficiency. | To replace traditional hardware-based network functions with software-based, virtualized equivalents. |
| Relationship | NFV is the enabling architecture that allows VNFs to be deployed and managed. | VNFs are the building blocks or the actual virtualized network functions that run within the NFV environment. |
| Example | NFV provides the environment where VNFs like virtual firewalls or routers operate, along with orchestration and management tools. | A VNF could be a virtual firewall, virtual router, or virtual load balancer running on standard hardware within the NFV infrastructure. |
| Dependency | NFV can exist without a specific VNF, as it is a broader architecture. | VNFs depend on the NFV framework to be deployed, managed, and operated. |
