Table of Contents
Network address translation (NAT) is an age-old terminology. This is a service which enables private IP networks to use cloud and Internet. NAT does translation of Private IP addresses in an internal network to a public IP address to send packets to an external network or Internet. It operates on a router or edge platform and lets private networks connect to public networks and enables use of one single IP address to be shared by several hosts with IP and port translation.
Today we look more in detail about Cloud NAT, how it is used, its benefits, and how cloud NAT provides protection to the networks.
What is Cloud NAT?
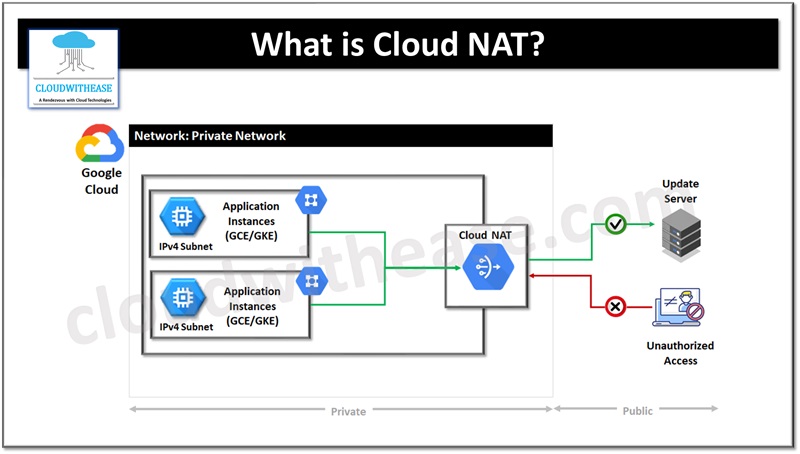
Network address translation (NAT) provides local area network (LAN) a set of IP addresses for internal traffic and another set of IP addresses for external traffic. Nat allows single IP address communication. Cloud NAT supports Google Cloud engine (GCE) virtual machine instances and Google Kubernetes Engine (GKE) containers with manual mode and auto mode. Manual mode lets developers specify the IP address and auto mode lets IP address allocation happen automatically.
Cloud Nat has no traditional proxy NAT configuration, the path from instance to its destination has no NAT proxy in-between. Each instance is allocated a unique set of NAT IP addresses and port range which is used by Google network virtualization stack (Andromeda) to perform NAT functions.
Cloud NAT is a software defined network service which uses cloud router resources for grouping the NAT gateway configuration. Andromeda created NAT allows an instance to use cloud NAT as much bandwidth as a virtual machine instance with an external IP address and NAT gateway and do not impact the performance of a cloud router.
Features of Cloud NAT
- Virtual machine instances and Google Kubernetes engine (GKE) clusters can connect Internet without external IP addresses.
- Any services running within the network are inaccessible outside the network hence this tremendously improvise security.
- No user management and intervention needed to provide high availability using cloud NAT. Failure in cloud NAT gateway or cloud router do not impact NAT configuration or capability of host to perform NAT.
- Cloud NAT are scalable and scale up with network traffic volume and number of instances.
- The number of instances does not impact the availability of network bandwidth as it automatically scales up required resources to accommodate traffic originating from instances.
Related:
Traditional Proxy NAT vs Cloud NAT
Network Protection with Cloud NAT
Imagine you have a multi-tier application hosted in the cloud. You want internal instances or servers to have outbound access for updates, patching, configuration management without having an external IP address so that you can keep your instances internal facing totally for better control. cloud NAT is an answer to this. Cloud NAT gateway routes traffic and let multiple virtual machine instances in a subnet reach use one single public IP address to reach the Internet.
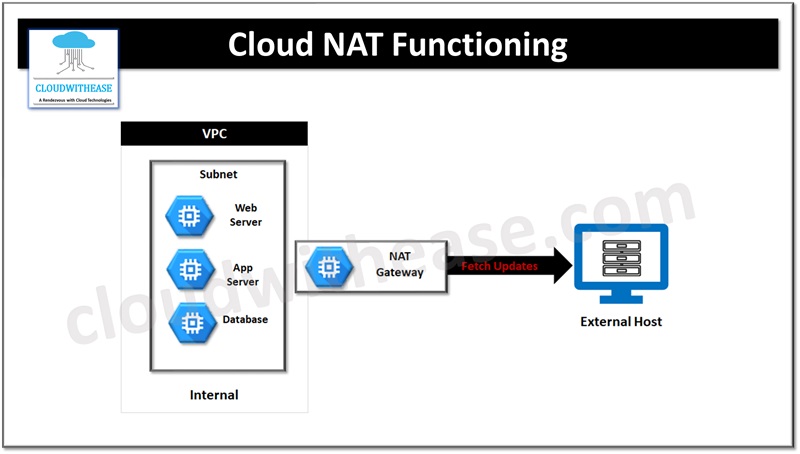
Google NAT does not use proxy and each internal instance is given a unique set of NAT IP addresses and port range. Which is used by Google network virtualization stack called Andromeda to implement NAT. There are no choke points, improved scalability, availability of network without compromising its performance. Cloud NAT can seamlessly scale with number of instances and network traffic volume. Instances get bandwidth as if they have assigned an external IP address.
- Provisioning virtual machines with public IP address means reduction in network attack surface
- Cloud NAT does not have any firewall rule requirements. Firewall rules are applied directly onto the network interface of compute engine virtual machines instead of cloud NAT gateway
- No special firewall rule creation required to allow connections to and from cloud NAT gateway when cloud NAT gateway provides NAT to virtual machine network interface and egress firewall rule is evaluated for the network interface before NAT. Ingress firewall rule evaluation happens post packets are processed by NAT.
