Table of Contents
Security of web traffic is of paramount importance for enterprises. Modern day network infrastructures rely on Secure web proxy which provides a secure, monitor and control web egress traffic in an organization network. Secure web proxy offers a wide variety of features to protect and control HTTPS traffic and act as gateway for clients and processes requests from various resources including virtual machine instances, containers, serverless environments and workload outside cloud connectivity via cloud VPN or cloud interconnect.
Today we look more in detail about secure web proxy, why we need it, how it works, common use cases for secure proxy, operational benefits etc.
What is Secure Web Proxy?
Secure web proxy is cloud platform (GCP) managed new service which is meant to control and protect egress (HTTP/S) traffic. The service works as a gateway for clients, perform processing of varied resources in cloud computing environments. Web proxy functions as an intermediary to clients seeking resources and acts as a shield of protection between servers and the Internet. Policies based on first cloud identities and web applications are supported at granular level for control and flexibility.
Reasons to use Secure Web Proxy
A secure web proxy is required for several reasons as under:
- Security – Provides an additional layer of security and handles requests on behalf of servers and hides their internal details. It prevents unauthorized access and provides protection to the network from cyber-attacks.
- Filtering – Internet usage is regulated by blocking access to specific sites or content. Majorly useful in enterprise organizations and helps to enforce internet use policies
- Caching – Proxies store frequently visited web pages thus provide quick access to multiple users looking at similar pages from cache itself and helps to improve response time and reduce usage of bandwidth.
Design and Working of Secure Web Proxy
Hub and Spoke design with a shared secure web proxy is ideal for large scale cloud deployments as it enables centralized management and better security controls. The secure web proxy will be implemented on the hub in the network to ensure all egress traffic from spoke networks channelized via Secure web proxy to control and inspect. The filtering shall be applied on secured (HTTP/S, TLS) and non-secured (HTTP) traffic.
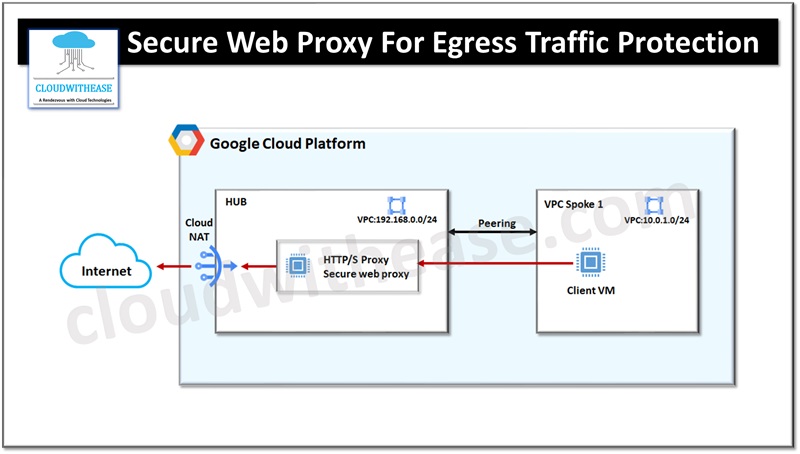
All internet access from spokes must be using static IP address using Google Cloud NAT to enable interfaces to access the Internet without external IP addresses.
Workloads are configured to use a secure web proxy to act as a gateway. Web requests could originate from virtual machine instances, containers, serverless environments, and workloads which are outside the cloud ecosystem. Policies applied in cloud SWP apply to traffic sent to workloads from outside (Internet).
Cloud SWP enables organizations to implement access policies at granular level and limit egress web traffic based on its source, identities, destination, or type of requests. Policies can be created using Cloud SWP with Google Identity and access management (IAM) context for blocking egress using service accounts and secure tags. Secure web proxy provides scalable TLS inspection service to enable TLS traffic interception and enforcement of policies. Cloud logging and cloud metrics monitoring can be integrated to maintain transaction logs of requests handled by proxy.
Common Use Cases for Secure Web Proxy
- Restriction on workload access to only selected trusted external web sites
- Monitoring outbound access
- Monitoring of usage, discover and disrupt threats
- Aid in forensic investigations of security events and incidents where egress traffic is involved
Operational Benefits of Secure Web Proxy
Secure web proxy works like a managed service and is quite different from traditional proxy solutions.
- It does not require configuration of virtual machines to run and scale the proxy. Patching for security threats is handled automatically.
- It is scalable and helps to take care of business growing needs.
- It helps to make cloud migrations seamless. Existing proxy policies can be ported as-is to cloud SWP while doing application migration from on prem deployment to cloud deployment.
- Secure proxy log can be integrated with cloud logging and monitoring to enable collection and analysis of logs and metrics for egress network traffic.

