Table of Contents
In today’s fast-paced digital landscape, more and more enterprises are embracing cloud-native technologies and containerization to drive innovation, enhance scalability, and streamline application development. However, with the increasing adoption of cloud-native platforms like Kubernetes, the need for robust security measures has become paramount.
In this article, we will explore the 4 Cs (Cloud, Cluster, Container, Code) of cloud-native security and discuss best practices to mitigate common security risks. So, let’s dive in!
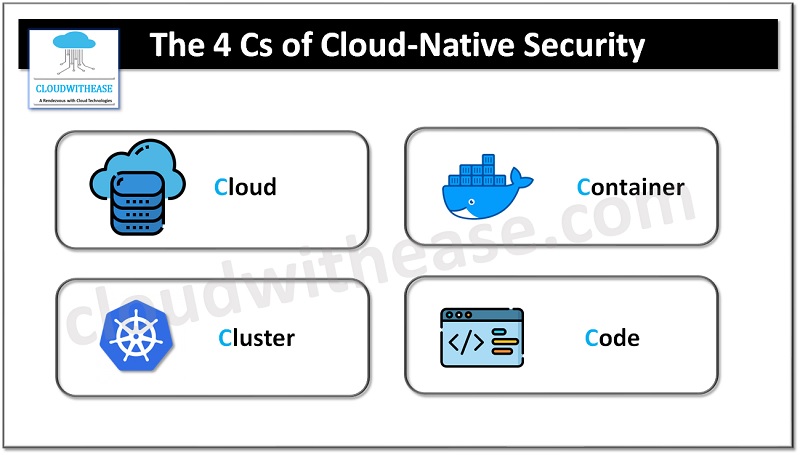
Cloud Security: Protecting the Foundation
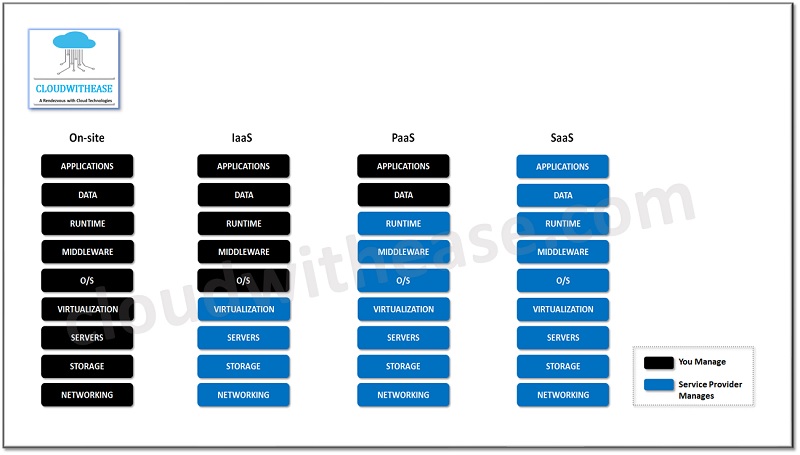
The cloud serves as the foundation for all security layers in a cloud-native environment. While cloud service providers (CSPs) are responsible for building a secure underlying infrastructure, organizations must understand the shared responsibility model for cloud security. Cloud security is not just about setting up a secure cloud; it’s about using it securely.
Common Cloud Security Issues
- Lack of visibility into cloud data: Businesses need to be accountable for knowing what information is stored in the cloud, who has access to it, and what security measures have been implemented.
- Security system misconfigurations: Misconfigurations in cloud network security systems can leave critical customer data and applications vulnerable to attacks.
- Theft of data from cloud applications: Data protection is crucial in a cloud environment, as malicious actors can exploit vulnerabilities to steal sensitive information.
- Inadequate staff with the skills to manage cloud security: Migrating to the cloud requires specialized skills for the proper planning, assessment, migration, deployment, management, and optimization of cloud solutions.
Mitigating Cloud Computing Security Issues
To mitigate cloud computing security risks, organizations should consider the following best practices:
- Adopting DevSecOps processes: Integrating security practices into the development and operations processes helps identify and address security issues early in the software development lifecycle.
- Leveraging automated application deployment and management tools: Automation can streamline security processes and ensure consistent security configurations across the cloud environment.
- Implementing unified security with centralized management: Centralized management allows organizations to have better visibility and control over their cloud services and providers.
- Understanding the security framework of cloud service providers: Familiarize yourself with the security measures provided by your CSP and ensure they align with your organization’s security requirements.
Cluster Security: Securing the Orchestrator
At the cluster layer, organizations need to focus on securing the container orchestration tool, Kubernetes. Proper access control, cluster configurations, and network security are crucial to ensure the integrity and availability of the cluster.
Key Considerations for Cluster Security
- Insufficient access control for cluster components: Weak access control can lead to unauthorized access and compromises within the cluster. It’s important to manage API server access and limit direct access to etcd, the key-value store used by Kubernetes.
- Cluster misconfigurations: Proper configuration of cluster nodes and access controls is essential. Implement access-allow lists and manage clusters according to the least-privilege principle.
- Poor cluster networking: Secure communication between containers, pods, and services using container network interfaces (CNIs) and network policies. This helps control traffic and prevent unwanted communication within the cluster.
Container Security: Protecting the Workloads
Containers play a vital role in cloud-native environments, enabling organizations to package applications and dependencies into portable and isolated units. However, securing containers requires ongoing efforts to mitigate potential vulnerabilities.
Ensuring Container Security
When it comes to container security, organizations should consider the following aspects:
- Building secure container images: Avoid using the root user and apply the least privilege principle when creating container images.
- Vulnerability scanning: Regularly scan containerized applications for vulnerabilities and exposures, ensuring that even the dependencies outside of OS packages are thoroughly inspected.
- Container image signing: Sign container images to ensure their integrity and build trust. Image signing technologies like TUF or Notary can help establish a system of trust for the contents of containers.
Code Security: Developer’s Responsibility
At the code level, organizations have the most control over security. By implementing secure coding practices and employing various security testing techniques, organizations can mitigate risks and protect their cloud-native applications.
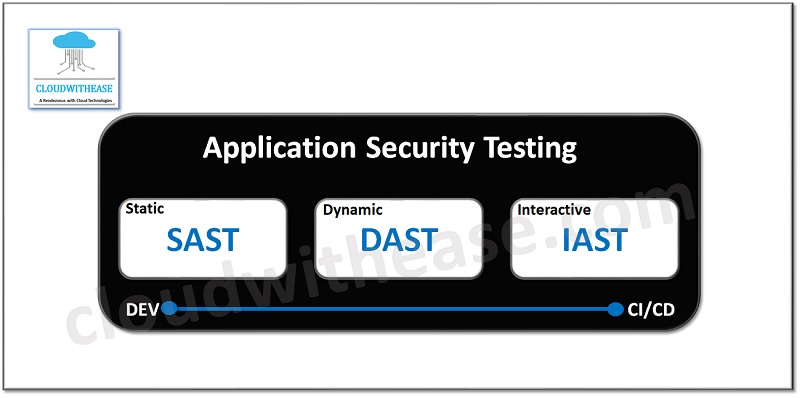
Enhancing Code Security
Developers play a crucial role in ensuring code security. Here are some key practices to consider:
- Static Application Security Testing (SAST): Utilize static code analysis tools to identify security flaws and vulnerabilities in code during the development pipeline.
- Dynamic Application Security Testing (DAST): Regularly run automated scans and tests to identify and address common application threats, such as SQL injection and cross-site scripting.
- Interactive Application Security Testing (IAST): Verify the security of software dependencies, such as libraries, by using tools like OWASP dependency check.
Conclusion: Cloud-Native Security
In today’s digital landscape, cloud-native technologies and containerization offer numerous benefits to enterprises. However, with these benefits come security challenges. By adopting a defense-in-depth approach and implementing security measures at each layer, cloud, cluster, container, and code; organizations can mitigate risks and build robust and secure cloud-native applications.
Remember, security vulnerabilities are not limited to hardware and software; human error and negligence also pose significant risks. Therefore, it is crucial to develop a holistic security strategy that addresses all possible threats and ensures the protection of systems and data.
By following the best practices outlined in this guide, organizations can enhance the security of their cloud-native applications and stay one step ahead of potential threats. Embrace the 4 Cs of cloud-native security and build a resilient and secure cloud-native ecosystem for your organization.
